This section covers the issues involved in filtering HTTPS sites and offers advice on how to manage those sites.
There are a number of significant differences in the way that HTTP and HTTPS sites are handled, and we recommend investigating implementing HTTPS decryption at your school in order to have greater control over your filtering. HTTPS decryption is part of the SchoolProtect service available to all LGfL schools and, with the launch of the new platform, is an area that has significantly evolved.
Summary
What is HTTPS Decryption?
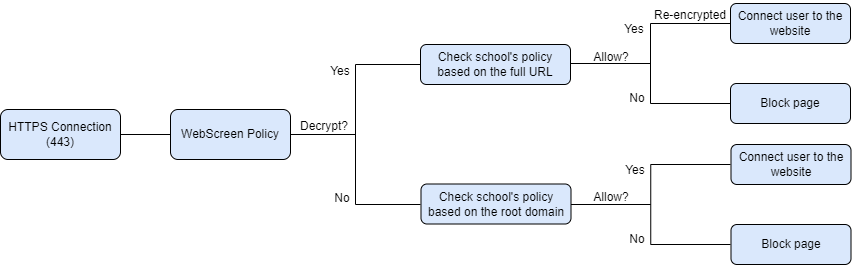
HTTPS decryption involves the SchoolProtect proxy servers decrypting and re-encrypting HTTPS session to view the content contained within.
Your network manager or IT support organisation will have previously installed an LGfL certificate to allow enhanced filtering functionality.
HTTPS decryption works seamlessly on managed devices once the certificate has been installed and relevant exclusions have been added as detailed in this guide, however, BYoD devices will either need the certificate installing manually on each device or added to an excluded IP range or policy. The school will need to decide what level of filtering to apply to BYoD devices. A common approach is to enforce decryption on student devices but not on staff devices.
A not encrypted HTTP website and an encrypted HTTPS website.
Why is it important?
HTTPS decryption is important for several reasons including:
•It grants the ability to allow or block individual pages, or areas, of a website. For example you could block Twitter, but allow the school's Twitter feed or allow BBC but block certain problematic areas of it.
•It enhances reporting. You'll be able to report on certain things that you wouldn't normally be able to such as the particular YouTube video a student has watched.
•It offers greater control over keywords. We recommend only using these sparingly, but you could block a troublesome term from being searched on Google.
•Using HTTPS Decryption means you will always be served with a block page on a blocked website, even when visiting HTTPS websites that are blocked. Without HTTPS decryption, these pages will display a 'page cannot be displayed' message. It will therefore it will be unclear why you can not access the website (a website could not display for a multitude of reasons) and if it was blocked by filtering, you'd be unable to see the information on the block page that will be helpful for troubleshooting.
•It will allow your school to use advanced SchoolProtect features such as greater control over embedded content.
So, how do I enable it for my school?
We strongly recommend enabling decryption, but it is something that should be done cautiously. We would recommend taking the following steps:
1.Research the topic.
2.Plan how you intend to roll it out in your school.
3.Install the HTTPS certificate on your devices.
4.Test, Monitor and make adjustments to your filtering.
5.Enabling HTTPS Decryption.
Setting up HTTPS Decryption at your school
1. Research
HTTPS Decryption can be a complicated topic. It's vital to read the documentation available in order to fully understand the implications of enabling HTTPS Decryption and what's involved to roll it out. An FAQ is below. Please note if you do have any questions or encounter any issues, our Support Team is on hand to assist.
FAQ
What types of websites will be decrypted? |
All websites will be decrypted apart from those that are under the default exclusion list and anything you add to your school's exclusion list. The full list can be seen by going to Policies >> HTTPS Decryption, clicking on Next, and at the bottom of the page you will see a button called See Decrypted Defaults. |
You might have some problems |
It will require some technical knowledge. We'd recommend working with your IT team.
It may be difficult to install certificates onto BYOD (Bring Your Own Devices). If HTTPS Decryption is enabled, most users will not know that their devices will need to have a certificate installed to be able to browse the web without having certificate errors. The solution to this would be to disable the HTTPS Decryption on the policy that the Wi-Fi is on, assuming that the mobile devices will connect to the internet via Wi-Fi.
There will be some sites that does not like to be decrypted and it may stop some of your products or services from working correctly, we do have a default list of websites that were do not recommend the school decrypt such as bank sites but this will not cover all possible sites that your product/service will need, this means that you may need to exclude some websites from being decrypted by going to Policies >> HTTPS Decryption then the Advanced tab. |
Concerns over HTTPS Decryption risking security |
Nothing you type on a web page, including your passwords and personal information, will be visible to LGfL or anyone else. We exempt financial services from being decrypted. |
What's different with the new decryption |
Before it was just Google that was decrypted. Now everything is decrypted except for exclusions. |
2. Plan
Like with any big change, we don't recommend rolling it out to everyone straight away. As highlighted above you might have some problems.
We would recommend rolling it out slowly. You can create policies targeted at any number of users or IP addresses, and so an effective way of rolling it out would be to initially enable HTTPS decryption on policies that would affect a small number of users, monitor and then roll out.
Think about which policies you do ultimately want to decrypt. If your school's Wi-Fi range for example is going to be frequently accessed by BYOD then perhaps it is best not to decrypt it (or at least provide instructions and a means for them obtaining the certificate).
3. Installing Certificates
It's very important that the certificate is installed on any device being decrypted otherwise you will have a degraded filtering experience. This includes uses receiving messages regarding "suspicious certificates" or any other certificate errors.
The certificate can be downloaded by anyone needing it from https://support.lgfl.org.uk/public/sslfiltx.crt
Please view this page for details on installing certificates. There are multiple options available from rolling the certificate our centrally to installing it on individual devices. It is essential that certificates are installed or measures to prepare users to do this themselves are undertaken before the service is enabled. You can roll out the certificate to any device before time without any risk.
4. Testing, monitor, making adjustments
Testing applications & devices
You should create a policy that can be used to test the websites, applications and devices in use at your school.
To do this:
1.Log into SchoolProtect and go to Policies > Policy Configuration.
2.Create a new policy and choose one of your existing policies (My establishment) as the source.
3.Open the Settings > IP Definitions page and create a new IP range to cover your testing device(s) linked to the policy you just created.
4.Go to Policies > HTTPS Decryption and toggle the Enable HTTPS Decryption switch for the policy.
5.HTTPS decryption will be active after a few minutes. Ensure your device(s) have the certificate installed and begin your testing.
What to test
It is suggested that you run the following tests before enabling further policies:
•Ensure the devices boot up and connects to the internet without errors.
•Make sure the devices can be managed by the MDM/cloud platform (e.g. Windows Azure AD/Google Admin Console)
•Run OS updates/upgrades on the devices and ensure these download correctly.
•Connect a device which has not been set up/enrolled in MDM/AD and determine if these can be enrolled without errors. Note: You may need to keep an IP range excluded from decryption for this purpose.
•Open each application and ensure they can log in and function correctly.
•Run application updates to ensure they download correctly.
As well as testing user devices such as PCs, mobiles, tablets, Chromebooks, etc., make sure you test other internet connected devices, for example:
•Printers
•Cameras
•Phone systems & handsets
•Building management (e.g. door controllers, heating systems, etc.)
•Connected alarm systems (e.g. fire alarms, intruder alarms, etc.)
Devices that are not used to browse the internet can be completely excluded from decryption, either by including them in a policy that does not have HTTPS decryption enabled or by adding IP exclusions as explained in the next section.
Most websites will not be affected by enabling HTTPS decryption if the certificate is installed on the system, however, it is best to check sites that the school relies on such as your MIS, cloud provider or payments systems.
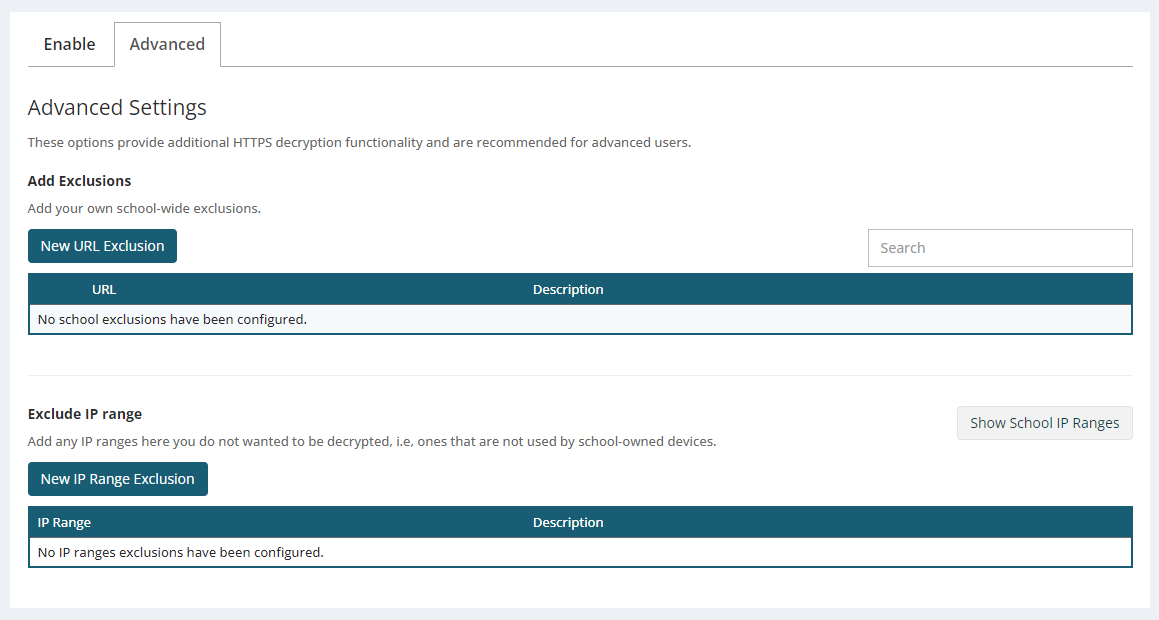
Adding exclusions
Excluding domains
Your testing will likely highlight certain domains that need to be excluded from decryption. These can be added to your school exclusion list.
1.In SchoolProtect, open the Policies > HTTPS Decryption page.
2.Under the Advanced tab, use the New URL Exclusion button to add identified domains to your exception list.
Excluding IP addresses
You can also add IP addresses or ranges to completely bypass decryption for certain devices. This works best for internet-of-things devices that aren’t used to browse the internet. You may need to set static IP addresses or DHCP reservations for your devices to ensure they keep the same address.
1.In SchoolProtect, open the Policies > HTTPS Decryption page.
2.Under the Advanced tab, use the New IP Range Exclusion button to add IP addresses or ranges to be excluded from decryption completely.
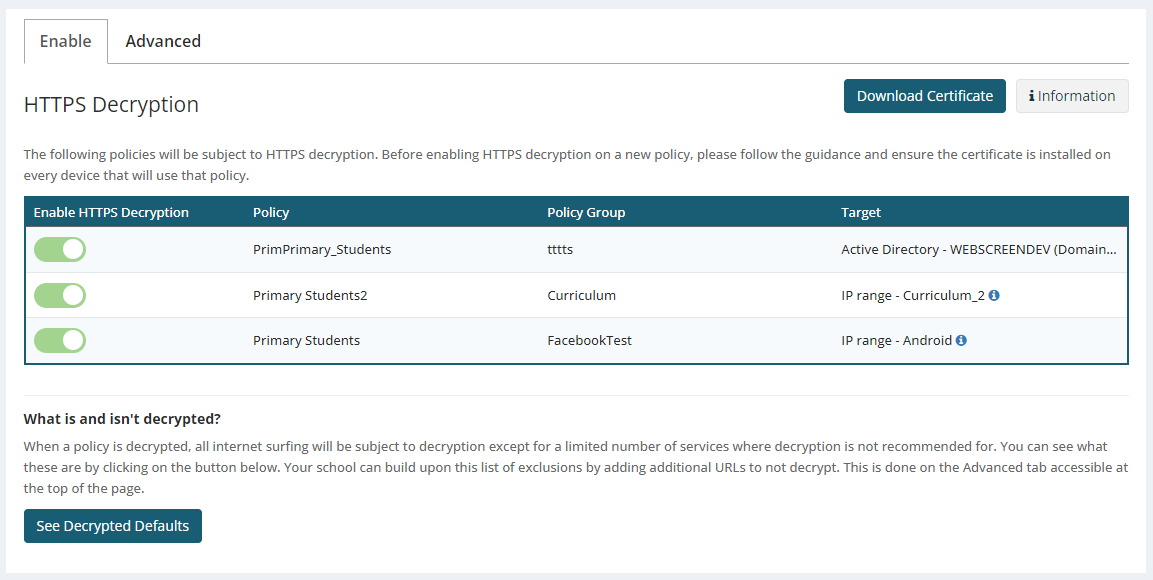
5. Enabling Decryption
Once you have tested your devices and applications and added the required exclusions, you can start turning on decryption for your policies.
From the Policies > HTTPS Decryption page in SchoolProtect, simply use the toggle buttons next to each policy to enable decryption.
By clicking on the See Decrypted Defaults button at the bottom of the page you can view all the websites that are currently in our default exclusion list (we do not decrypt these websites).
Also see: